This is default featured slide 1 title
Go to Blogger edit html and find these sentences.Now replace these sentences with your own descriptions.
This is default featured slide 2 title
Go to Blogger edit html and find these sentences.Now replace these sentences with your own descriptions.
This is default featured slide 3 title
Go to Blogger edit html and find these sentences.Now replace these sentences with your own descriptions.
This is default featured slide 4 title
Go to Blogger edit html and find these sentences.Now replace these sentences with your own descriptions.
This is default featured slide 5 title
Go to Blogger edit html and find these sentences.Now replace these sentences with your own descriptions.
Saturday 3 August 2013
Firepower The New Network Security Option Of Sourcefire FirePOWER Sourcefire, the security specialist has announced details about the enhancements for its network security platform of FirePOWER. It offers intrusion prevention, a fire wall as well as a solution against malware. All these are offered in a package that is hardware-based. Its aim is to provide protection without affecting performance. Approach of separate-box makes it simple and easy to add protection to existing networks and it is easily scalable in order to adapt to organizations of various sizes. Enhancements you find in this latest version include intrusion and firewall prevention systems which have better support for IPv6 and also product awareness. Policy on Network address translation could now be set centrally instead of by device. This allows for consistent approach across an organization. Cloud intelligence is used by threat protection of the product in order to have it updated and stay up to date. Event analysis reports have been added with geolocation. This gives administrators more information with regard to the region of the websites that are being visited. New features on site-to-site VPN allows secure communication when Sourcefire protected networks communicate between one another. In addition to that features that are of high availability for firewall make sure that that disruption is minimal. Even following a device failure the protection will continue. According to Martin Roesch the founder of Sourcefire and its CTO, present day organizations are faced with a growing number of persistent threats that are also sophisticated, to their corporate data. This increases the demand for scalable and flexible security solutions which could be customized in order to deliver protection optimized for the environments of customers. With the present enhancements to their FirePOWER platform customers of Sourcefire could be assured that they are able to access a security solution that delivers continuous protection before an attack, during one or even after an attack. More information could be obtained from the website of FirePOWER.
Sourcefire, the security specialist has announced details about the enhancements for its network security platform of FirePOWER. It offers intrusion prevention, a fire wall as well as a solution against malware. All these are offered in a package that is hardware-based. Its aim is to provide protection without affecting performance.
Approach of separate-box makes it simple and easy to add protection to existing networks and it is easily scalable in order to adapt to organizations of various sizes. Enhancements you find in this latest version include intrusion and firewall prevention systems which have better support for IPv6 and also product awareness. Policy on Network address translation could now be set centrally instead of by device. This allows for consistent approach across an organization. Cloud intelligence is used by threat protection of the product in order to have it updated and stay up to date.
Event analysis reports have been added with geolocation. This gives administrators more information with regard to the region of the websites that are being visited. New features on site-to-site VPN allows secure communication when Sourcefire protected networks communicate between one another. In addition to that features that are of high availability for firewall make sure that that disruption is minimal. Even following a device failure the protection will continue.
According to Martin Roesch the founder of Sourcefire and its CTO, present day organizations are faced with a growing number of persistent threats that are also sophisticated, to their corporate data. This increases the demand for scalable and flexible security solutions which could be customized in order to deliver protection optimized for the environments of customers. With the present enhancements to their FirePOWER platform customers of Sourcefire could be assured that they are able to access a security solution that delivers continuous protection before an attack, during one or even after an attack.
More information could be obtained from the website of FirePOWER.
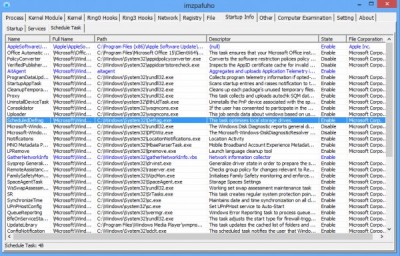
Use Powertool Analyze Windows And Apps And Troubleshoot Them
When you find problems with Windows, very often you could look at the Task Manager and find the programs that use too much of CPU time or RAM, for terminating the process that causes problems to normalize things.
Often you will find that Task Manager is unable to handle situations and it is necessary to have a third party tool and PowerTool is the one to have.
PowerTool developed by developers of PC Hunter could be used to look at different aspects of the system setup. Browse the interface with tabs to find lists of processes that are running, start up programs, loaded modules, windows services and more.
There are modules that are more active that include simple versions of Explorer as well as REGEDIT with which you could manipulate registry keys and files. Also you could view them.
Further options could be seen when you right click the lists. It is not only the displaying of running processes that PowerTool does. It also could look for malware at VirusTotal and force them to terminate if problems are there. It could even delete them to prevent them from restarting.
Story is the same with services of Windows. It could manually stop them and restart. Also, set up the startup type of them and do lot more.
You also could view details such as kernel threads as well as notifying routines, SSDT as well as Shadow SSDT hooks, filters, and more. Memory dumps could be initiated and hooks could be restored. Even changing the protection of RAM blocks or editing them manually could be done.
There are also bad news with PowerTool. The interface doesn’t always work the way you want. For instance, you cannot view more details with double click or with right clicks on properties. We have also experienced crashing of registry browser with one test system.
Overall, as Process Explorer says PowerTool is not a polished program. But is powerful and comes free with no strings. To hunt malware manually and to know what is taking place in your PC at a low level it is a good program. Have a look.awaisakh.blogspot.com
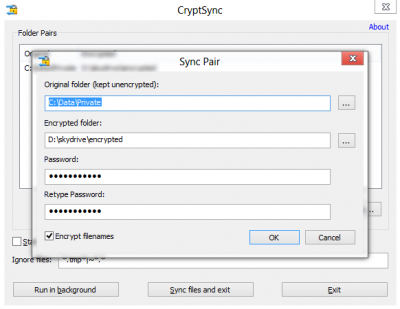
All Your Cloud Storage Files Could Be Easily Encrypted With Cryptsync
It is convenient to store your important files online but there is a security risk to manage when you do so. Though encryption is offered by the cloud service of yours there is no guarantee that no one is able to steal your password. If that happens, your data will get exposed.
The best way to maintain privacy of your files is to encrypt them before you do the uploading. Since this will provide extra protection no attacker will be able to look at your files. When you use open source software of CryptSync your problem will be solved and the software will do the job almost automatically.
The program sets up folders in pairs. A source folder will have your files in the unencrypted version and the destination folder will have the encrypted files. Any files you store in the source folder will be encrypted using 7-Zip and then synced to the destination file for uploading to the web.
The synchronization works on either way. If a file in the encrypted folder is changed CryptSync will create its unencrypted version in the source folder. Though it is the default setting you could change it if you want. Then you will mirror contents of one to the other folder.
However, it is obvious that there are complications. In case the cloud files of yours are encrypted you won’t be able to access them with any browser or a device. You will need a device to do the decryption.
When you use CryptSync it is not a must for you to encrypt all your files that will go online. While the program could be used for encrypting your important files, your media files could be left without being encrypted. This will allow you to stream music though you may find it difficult to use other files.
All things considered, CryptSync awaisakh.blogspot.com provides you with extra protection which also is automatic to a great extent. As such, if you are serious about the privacy of your cloud storage files you may consider using this program.
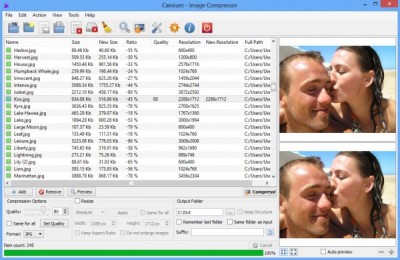
Batch Compress Your JPEGs Up To 90% With Caesium
In case you save a JPEG image, the easy way is to accept the default option on the image by clicking File>Save. This means you are using the JPEG compression level that existed without changing it. Unless you change the compression to an optimum level the final image of yours will probably become ten times the size you really need.
Caesium, an open source program offers an easy way to find if this is going to be a problem for you. You can point this program at images you select or a folder that has them. It will recompress the files quickly to a lower setting on quality. The program supports PNG, WMF, BMP and JPG files. Once the compression is done, it will also provide you a report.
This process is not difficult to set up. You can import images with a click. The slider offers to set up the compression level anew. The recompressed images could be saved in a new one or the same folder.
In case you need to share photos with others by having a lower resolution, you could use the program’s optional tool for image resizing.
On performance of the software we have found JPEG results to be generally 30 to 90 percent good. Around 10% of the images stayed the same size virtually and some got larger.
Compression of PNG was poor relatively and most of the images tested have increased in size. (Though this is a disappointment it will not affect your files as you could tell the program not to save the images recompressed if they become larger than their originals).
You cannot predict the results obtained with Caesium and everything depends on the source images. In case you want to shrink JPEG images you will find that it is a successful program. However, it will take only 10 minutes to know what happened. So better download a copy to see what Caesium could do for you.
Create Internet Video In A Simple Way With Easyflv Web Video Encoder
Conversion of videos into a web-friendly format is not such a difficult task as there are many different transcording tools. These could import source movies and convert them to WEBM or FLV format.
If you are one who does conversion of videos frequently a specialist tool such as EasyFLV Web Video Encorder could be useful. It is easy to use and has some extras that could save time.
Its interface is straightforward and has all options in one dialog. When you select your video and click on “Start Encoding” it will start the job.
You need to fine tune things with EasyFLV Web Video Encorder but it is a simple program that offers only the essential options.
Some bonus options are there with this program. It could export MP4, FLV and WEBM videos but it is not necessary to choose one. When you check all three check boxes you will get your video in all three formats.
In order to customize your video you could add a watermark on your video also with EasyFLV Web Video Encoder.
In case you like to have a still image to show the content of your video you could use any frame and not only the first one. It will be saved in JPG.
You can save a “profile” with any combination in order to reload later. If you want to encode different videos in different ways you only need to open the right profile. No need to reconfigure the program.
The program also has a “built-in moov atom fixer for MP4 to help you to get the moov atoms streamed on the web which are placed at the end of MP 4 files.
EasyFLV Web Video Encoder is a weak program. Only three output formats are there, and you have little control on the finished results.
If you want videos created for the web EasyFLV Web Video Encorder is good for you as you won’t suffer penalties or any problems with your computer. It will also help you save time.
Subscribe to:
Posts (Atom)